Overview
Today we’re going to go over the principals of wireless hacking, an example of a WPA2 hacking and then we will wrap it up with a few troubleshooting tips.
Disclaimer: Before we begin let me preface this. Intrusion into anyone’s network without express permission by the network owner is illegal. I highly recommend you practice these techniques on your own wireless network. I take NO responsibility in what you do with this knowledge.
Requirements
- Kali Linux (Installed onto a host or running in a VM)
- I’ll be using Kali in a VM from Hack Lab
- A wireless adapter that supports packet injection
- Here is a list of adapters I recommend. I’ll be using the [easyazon_link identifier=”B003YI4HRM” locale=”US” tag=”hackm01-20″]Alfa AWUS036H[/easyazon_link]
- A wireless router
- A good wordlist (Kali comes with Rockyou by default)
Note: If you have an onboard wireless card that supports packet injection and you’re using a VM you will have issues. Your VM will think that your host wireless adapter is actually a physical connection. In this case I would recommend just using a LiveCD or boot from a USB.
Note2: I’ve included some troubleshooting steps at the end
Principles/Tools of Wireless Hacking
Wireless hacking allows us to enter a network. Entering a network will allow us to see shares, capture network traffic, connect to other machines and enumerate within that network. It is akin to plugging a Ethernet cable from your computer into the switch of a network you do not own. Wireless hacking is a relatively simple process, essentially you’re just pulling information out of the air and decrypting it using the weakness in authentication processes.
Packet Injection
There isn’t much I can say on packet injection that hasn’t been already said on wikipedia but in the interest of making this a complete tutorial I’ll briefly describe what its all about.
Packet injection is exactly what it says. It allows you to create and send packets and inject them into the communication stream. This is what will allow you to send deauth packets and essentially DDoS a user’s wireless connection.
Airmon-ng
Airmon-ng is simply a script that enables your wireless interface to begin monitor mode.
Airodump-ng
This is used to actually capture the packets once your wireless interface is set to monitor mode. This is your collection of data. You’ll use this to collect packets to crack WEP and collect a WPA2 handshake.
Aircrack-ng
Aircrack cracks WEP, WPA and WPA-2 by using the input from Airodump-ng.
Pre-Setup
So first we’ll do a few small configurations to our hacklab. Mainly this is going to allow our VM’s to see our external wireless card.
Note: I’ll be doing this on my MacBook so my version of VirtualBox will look a little different.
1. Go into VirtualBox settings -> Ports -> Enable USB 2.0 Controller
2. Inside of your VirtualBox Kali machine on the bottom right corner click on the image of the USB and select your wireless USB adapter. Mine is called RTL8187_Wireless [0100] in this case. This passes the USB device into your virtual machine.
3. Now when you list your interfaces in your VM you should see you’re wireless card listed.
WPA2 Hacking Example
1. First we’re going to start the airmon-ng service for our wireless card interface. Take note about processes that could cause trouble.
2. Verify that airmon-ng is running and that it has created a monitor interface. Mine is called mon0
3. Now that our interface is set to monitor we can start airodump-ng to monitor wireless traffic. Type airodump-ng <monitor interface> to start. In my case its airodump-ng mon0. This will begin to list wireless devices, this includes access points, devices, phones etc. If you’re seeing a lot of traffic and the access point you’re trying to get to you can press tab and use the arrow keys to select a device. If you press m you can cycle through colors and if you press space you can pause the live capture.
I blurred out the mac’s because I’m a nice neighbor. 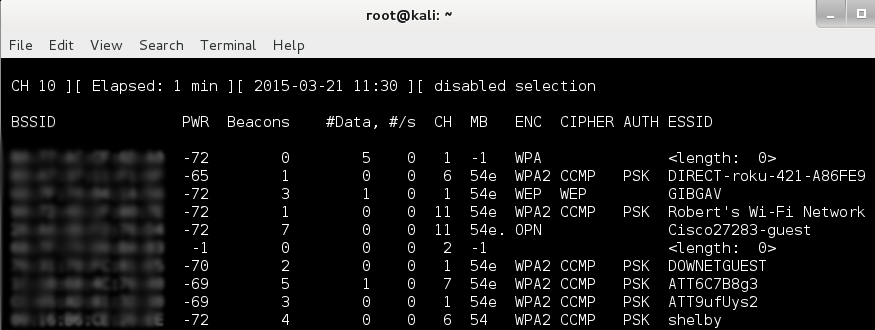
4. For the next step I’m going to target my own wireless router. I personally like to leave airodump-ng running in a separate tab with the feed paused so I can refer to it while I work in another terminal. Take note of the BSSID and the channel of the target wireless router and use the command syntax below.
airodump-ng –bssid <bssid> -c <channel> –write <filename> mon0
- –bssid: base station SSID for your target
- -c: channel device is on
- –write: the file you are dumping frames into
- mon0: monitoring interface of your VM
5. Next we’re going to to need to capture a WPA2 handshake. First we need someone to associate to the access point. The easiest and most common way to do this is to send de-authentication packets to the access point and require users to re-authenticate. Constantly sending deauth packets to someone is very similar to DDoSing someone. Do this in a separate tab.
- –deauth <# of deauth packets>
- -a BSSID of target
6. While deauthing you should notice your access point targeted airodump-ng tab has changed in the top right corner and will now say “WPA handshake” with the BSSID of the access point.
7. Now that you have a captured handshake its time to use aircrack-ng to crack the password. Note that the password must be in the wordlist you use and that if you use a wordlist that is very large this will take time. For the purposes of this exercise I put the password for my wireless access point into a file called passwords.txt and used that as my word list for the sake of demonstration.
aircrack-ng <airodump-ng filename.cap> -w <wordlist file>
Here is what it looks like while it is running:
And here is what it looks like when it is successful. I’ve included the command syntax that I used to run the command in the prompt as well.
Troubleshooting
Troubleshooting is pretty difficult because there are so many variables. Wireless card drivers being the big wildcard, check the aircrack-ng drivers support page and update accordingly.
I would also highly recommend updating your kali box, not just to correct issues with wireless cracking but it is best practice in general. To do so type ‘sudo apt-get update && apt-get upgrade’. For those interested && just means to apply command following it if the previous command was successful.
The best troubleshooting resource is the official FAQ and troubleshooting guide.
If during step four in the top right corner you’re seeing “fixed channel -1” you need to kill your network managers. Remember in step 1 where airmon-ng tells you that some process may give you trouble? Type “kill <pid>” to stop that process from running.
If you have any issues please post them in the comment below and I will do my best to help you troubleshoot!









