Linux Unified Key Setup, or LUKS [luhks] as it will be referred to as from here on out, is a widely used method of disk-encryption. LUKS is proprietary to the Linux Kernel and a device encrypted with LUKS will not mount in a Windows or Apple environment. LUKS can encrypt entire block devices such as Hard Disks Drives (HDD), Solid-State Devices (SSD) such as USB sticks or Flash drives, partitions, etc. LUKS is largely recommended for protecting removable storage media, laptop hard-disks or Linux swap files and not recommended for file level encryption.
In this tutorial I will be using the following:
- Oracle VirtualBox Version 5.1.8
- [easyazon_link identifier=”B00CIDILLM” locale=”US” tag=”hackm01-20″]Centon DataStick Sport 16GB USB 2.0 (S1-U2W1-16G)[/easyazon_link]
- Debian 4.0.4-1+Kali2
Kali 2.0 and Ubuntu 14.04 provides full support for LUKS encryption to encrypt block devices on the fly. Even if you are running a different flavor of linux it’s likely that they’re already present on your system, however, if you performed a minimal *nix install, chances are the per-requisites of cryptsetup (cryptsetup-luks for CentOS-5), device-mapper, and util-linux packages aren’t present on your system. To install them run the following command(s):
$ sudo apt-get install <package name> [On Debian Based Systems]# yum install <package name> [On RedHat Based Systems]
Follow the prompts for each line until installed. Once cryptsetup, device-mapper, and util-linux have been installed we can start. First thing’s first, plug in your flash drive and let’s make sure our flash drive has been detected.
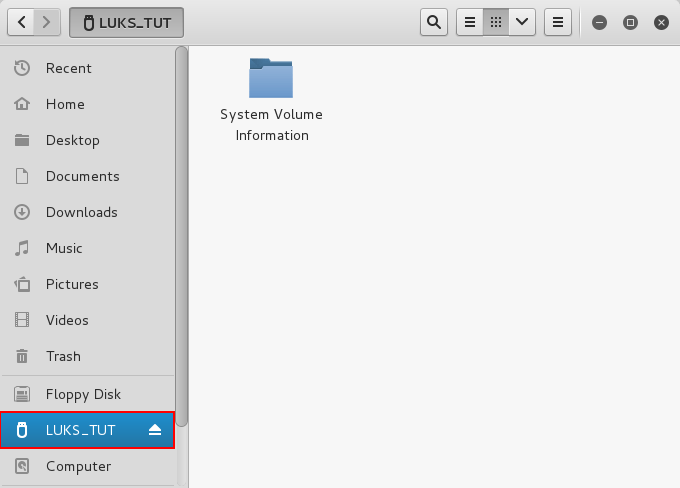
In the screenshot below we can see that the ‘LUKS_TUT’ USB device has been detected and we can verify by opening the ‘files’ icon on the left highlighted with a red box.
Upon opening the ‘files’ icon you will be presented with the below screen shot. Again highlighted in red is our ‘LUKS_TUT’ USB device attached.
From here, the task is quite simple. We right click on our ‘LUKS_TUT’ USB device and select Format... The pop-up we are presented with titled Format Volume is where we will select our settings. It should look something like the below screenshot.

With the Format Volume pop-up in view, select the Erase drop down menu, from there select Overwrite existing data with zeroes (Slow). This will wipe all data and 0 every byte on the device. Heads up, this will take a while to complete. If you are impatient or don’t have the time, select Don't overwrite existing data (Quick). Next move to the Type drop down menu and select Encrypted, compatible with Linux systems (LUKS + Ext4). The next few sections are personal preference, but for the sake of following along with the screenshot we named our device ‘ENC_LUKS_TUT’ and made our passphrase ‘incidrthreat’. When you have filled out all areas you should have something similar to the below screenshot.

When you are happy with the settings and you are certain you can remember your passphrase select Format... Once you do that you should be prompted with another warning and notice (See screenshot below). Again, if you are confident in your choices and have backed up any data you needed click Format

Upon completion, your USB device will reconnect unlocked. To test the encryption, you must unmount (remove) and reinsert your USB device. When the system attempts to remount the Encrypted USB device you are presented an input box to enter the passphrase you formated the drive with. If you look at the drive name, it is not the name you selected. This is bc the drive and name are encrypted. Below is what you should see.
Once you’ve entered your password you are given access to your very own encrypted USB device and the name you selected appears in place of the ’16 GB Encrypted’ name once displayed. Now only you have access (unless you share your passphrase with others). The only way for someone to make use of the encrypted drive without consent is to reformat the drive resulting in the loss of your data or in my case my Super Secret Folder. Not much to it, really quite simple.

If you have any questions or comments, please leave them below or email me at incidrthreat@gmail.com, even if it’s to tell me my grammar/editing sucks. We are always looking to improve the site and always looking for new tutorials to write/sponsor. Thanks for reading and happy hacking!


