Recap of Level 24: Created a little BASH script to cause a cron job.
Objective:
Brute force the server listening on port 30002 using the password for Bandit 24.
Intel Given:
- A daemon or service is listening on port 30002
- Sending the password for Bandit 24 plus a pin will cause the service to send us the correct password
- There are 10000 possible pins. 0-10000
How to:
First off a disclaimer: I am not a programmer. I don’t really have an official title, but I can be loosely called an incident handler/vulnerability re-mediator. I chose python as the language that I’m going to be learning and you can read why here. My code may not be the best, most elegant or feature rich. If you see anything you would change or I could do better please let me know! Shout out to RST for the assist in helping with a little newline issue.
We know there is a service running on the local machine on port 30002. If we were following the hacker methodology, we could nmap it try to discover the service and gain a bit more intel. Because we’re playing a game and we’re given some intel I’m going to assume this is a custom script being run on this port and I’m going to skip doing a service scan.
This list will be our general steps for this challenge/script.
- Connect to the service
- Send a password + pin combo (Script and automate this process)
- Evaluate the results
For Step 1, I like to use netcat to connect to services. Netcat is one of the primary tools for connecting to things in the hacker toolbox, often times if I reach for my [easyazon_link identifier=”1494295504″ locale=”US” tag=”hackm01-20″]Red Team Field Manual[/easyazon_link] its because I’m looking for a netcat switch.
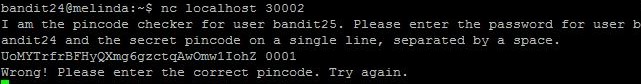
First off, lets connect. nc invokes the netcat command, localhost is the local machine and 30002 is the port we’re connecting to.

We are given a banner and more intel on the format of input. It wants the password plus the pincode on one line plus a space in-between. So lets try that and I see what happens.
When we input the password as requested we’re given an error message. This is also important because when we create our script we don’t know what the service or daemon will do with a correct answer, only an incorrect one. So we can use that error message to evaluate a condition in our script if we want. Spoiler: I didn’t, and you’ll see why.
We could continue manually entering these pins if we want but that would take us a really long time. So lets use the computer to do the manual labor for us an automate this process. You can use any scripting language you like, perl, bash, python. I originally solved it in bash and then python just to learn more about python.
A bit of setup is required, you can only write to the /tmp/ directory when logged into bandit and you can’t view the files. So you just need to create your own directory, mine is /tmp/r00ty for the sake of this exercise.
I’ll post the solution and then walk you through the script.
I had a few objectives. I knew I could pass commands to bash using the python library but that would basically be me just making a python/bash hybrid solution. I wanted this script to do everything from the connection to the brute force in python.
First I import the socket library, socket is required to make network connections. Then I initialize the pin variable with a 0 and set my password variable. Next I establish an object called ‘s’ which sets up my socket. I use the socket object and have it connect to ‘localhost’ on port ‘30002’ and then using s.recv(1024) accept the ‘banner’. So far this just established the connection to the service. Now we enter a while loop to brute force the password.
The while loop simply prints the pin it will attempt. Next, s.sendall() sends the password and pin through the socket. Note the ‘\n’ as the last argument to the function, this is required because it tells the service that you’re done entering a line, without it the script will hang. Finally we capture the data returned from the server, print it and increase the pin by one. Then it starts all over.
Now if I were to make this script more feature rich I could evaluate a condition to determine if the return from the service had “Wrong!” in it, if so continue the script. If not, stop and say ‘Pin Found!’. Luckily for me that was not needed because the service resets the connection when the correct pin is presented and thus the script stops.
Note: It’s been pointed out that my while loop is an infinity loop. I know, I could have just used a for loop and that’s a better method of doing it. I was planning on putting in error handling + conditionals but it wasn’t necessary.
Conclusion:
You could have gone about solving this problem in several ways with several different scripts. In fact your python script will probably look very different than mine (probably better too). We discussed how to connect to an unknown service and script a little pin brute force script. I hope that I have also showed you how python can be used to help automate tasks when doing some of these challenges on your own. Another example of a more feature rich script can be found here.